
What is So Critical About Critical Infrastructure?
Over the next several weeks we will be diving deeper and talking more extensively about the importance of protecting the nation’s critical infrastructure (CI), why it’s targeted, and how to defend against attacks. Hardly a day passes by without critical infrastructure attacks making headline news, whether on the U.S. CI or some other nation’s CI. It doesn’t matter. The CI Sectors are being attacked and the impacts have proven devastating. And as we are seeing during the 2022 Ukraine-Russia conflict, attacks on nations’ CIs have a global reach.
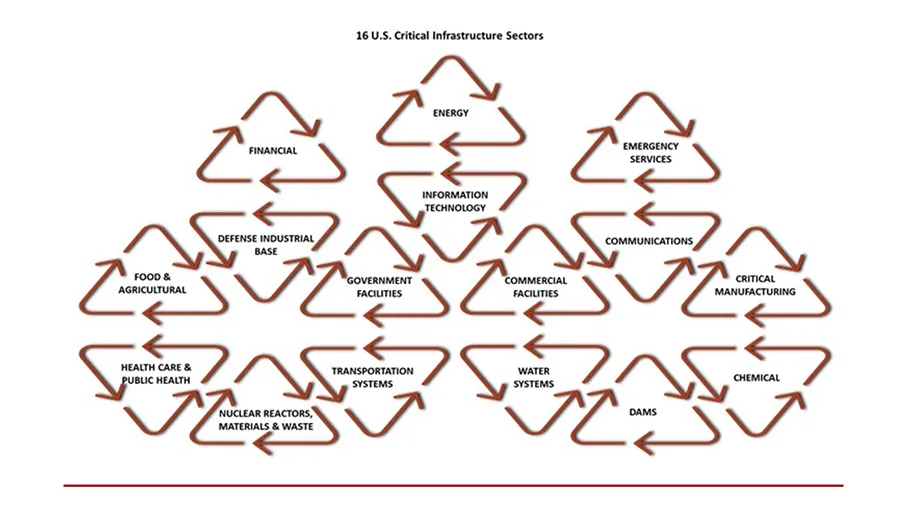
The Critical Infrastructure Sectors
Sixteen sectors make up the nation’s CI.¹ The incapacitation or destruction of any sector would have a devastating effect on national economic security, national public health, public safety, or any combination thereof.
They are dependent on each other. An attack on one sector can have devastating consequences for other sectors. The U.S. government has centralized strategies to ensure that CI Protection (CIP) is planned and implemented in a disciplined and unified manner.
The Nation’s Critical Infrastructure is Subject to Increasing Physical and Cyber Attacks. But Why?
CIP has been an increasing priority for the U.S. over the past couple decades. Due to the continuous number of attacks on the nation’s CI, the U.S. government has been making a concerted effort to develop strategies and plans for protecting CI. A common theme of these CI attacks has been that the infrastructure systems themselves were the target vice the data.
Attackers’ objective on CI is to disrupt the nation’s economic, social, political, and public health and safety to promote their own political, social, or financial goals.
In other words, business and mission IT systems manage information while industrial control systems (more on this in Part 2 of this series) manage physical operational functions. Attacks on CI are not focused on compromising data confidentiality, but rather focusing on compromising the integrity and availability of industrial control systems to meet their objectives.
An attack on these systems, whether via physical or cyber-attacks, can have devastating physical consequences for the U.S. public and private sectors.
As CI Sectors have become more connected, it has become easier for attackers to successfully exploit infrastructure vulnerabilities. Additionally, the Internet and technologies have allowed attackers to use cyber tactics, techniques, and procedures to conduct cyber-attacks, and in some cases overshadow physical attacks.
But don’t be convinced that those physical attacks are passe. Physical attacks on CI continue to be a preferred attack vector for many attackers.
Tracking Physical Attacks are Tangible. Tracking Cyber Attacks—Not So Much.
Critical Infrastructure Attacks: Physical and Cyber Attacks
Even going back 200 years, physical attacks were tangible, as they still are today. They can be tracked, studied, and countered with appropriate physical defenses. Classic examples include blowing up bridges and railroad tracks. However, it is much more difficult to track, study, and develop countermeasures against cyber-attacks.
Cyber-attack vectors change more often, in effect rendering in-place virtual countermeasures ineffective. In some cases, such as SolarWinds (which is within the Information Technology CI Sector), a cyber-attack on a CI Sector is not known until it is too late. In the case of the SolarWinds attack, it is important to highlight that it affected multiple CI Sectors.
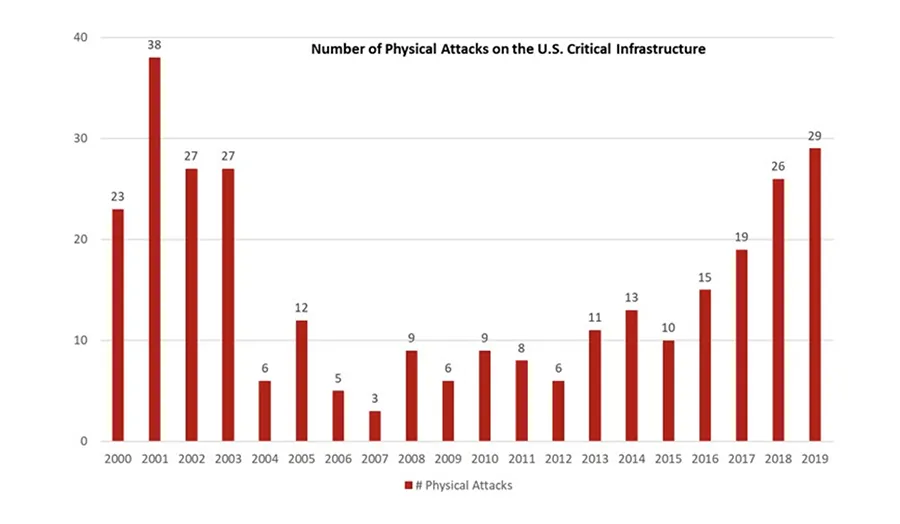
Physical Attacks on CI
Figure 2 illustrates the ebb and flow of successful physical attacks on the CI Sectors. Except for 9/11, most of these physical attacks resulted from domestic terrorism for political and social causes.² The U.S. continues to face an internal threat from political and social activists. Most of these physical attacks came against commercial business facilities and government facilities based on the social and political issues at the time.
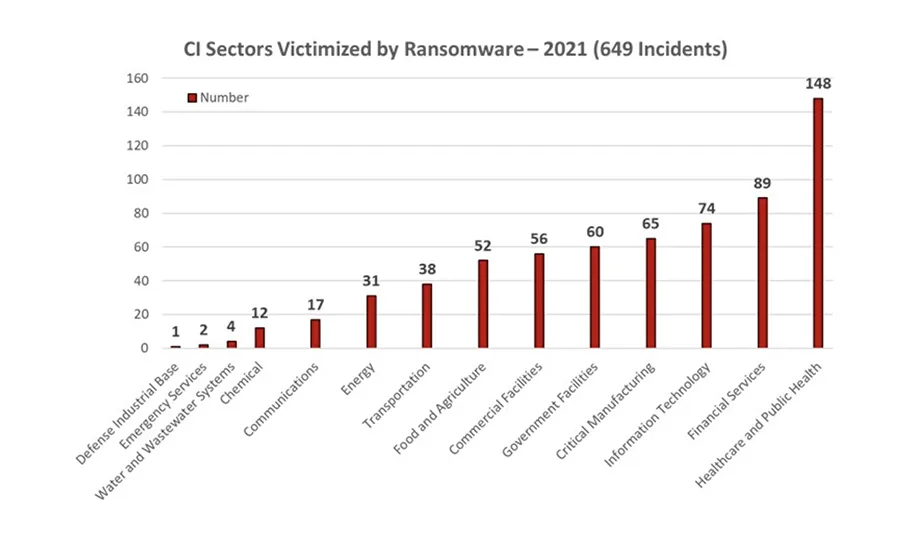
Cyber Attacks on CI
The threat of cyber-attacks has joined the long-standing threat of physical attacks. Between 2000 and 2022, the number of cyber-attacks on CI has grown exponentially.
By its very nature, virtual attacks are difficult to track for statistical purposes, however, based on empirical data over the past decade, it can be argued that cyber attacks on CI have significantly increased in a non-linear fashion, primarily due to the rapid adoption Internet-based technologies, such as the Internet of Things (IoT), Operational Technology (OT), and Supervisory Control and Data Acquisition systems (more on these in Part 2).
Critical Infrastructure Protection
Bottom Line: It’s Still About Fundamental Security Principles and Practices.
All organizations within each CI Sector must implement appropriate security measures for their CI sector or sectors (some may cross sectors), while not interfering with their ability or capability to continue conducting their mission or providing services. This is nothing new.
The effectiveness of security measures will rely on trusted threat intelligence and those likely threats that could potentially target its systems. This must include the most likely attack vectors against those systems, including how they are employed and operated (i.e., ICS, SCADA, IoT, OT, or a combination thereof).
In other words, know thy enemy. This is nothing new.
What is new is that the organization needs to understand how to protect their systems against attackers taking advantage of a virtually connected world that has cross-sector implications for the public and private sectors. Knowing the weak areas and protecting them before they can be exploited is critical.
The National Infrastructure Protection Plan
The U.S. government has many centralized resources to assist with CIP. The National Infrastructure Protection Plan (NIPP) outlines how government and private sector participants in the critical infrastructure community work together to manage risks and achieve security and resilience outcomes.⁴ The Cybersecurity and Infrastructure Security Agency (CISA) leads the effort to understand, manage, and reduce risk to the nation’s cyber and physical infrastructure. CISA provides resources, analyses, and tools to assist CI stakeholders to build and maintain their own cyber and physical security and resilience.
In Summary: Critical Infrastructure Security and Resilience
With the conveniences that a digitally connected world provides society, there also comes a price. A price that puts the nation in jeopardy. With ubiquitous connectivity comes exposed vulnerabilities. With exposed vulnerabilities, comes threat agents poking at those vulnerabilities. Poking around leads to successful attacks. With every successful attack (from the attacker’s perspective), comes consequences and the realization that additional countermeasures are needed. The trick is to slow down this cycle and minimize the impact when compromised. This routine must become muscle memory.
In Part 2, we will get into more detail and discuss the types of systems that make up the bulk of the nation’s CI. We will get into a little more detail on the acronym soup, like ICS, IoT, OT, and SCADA. Specifically, how they are targeted and how to protect them against virtual and physical attacks.
Sources
- Department of Homeland Security (DHS), Critical Infrastructure (CI) Definition: Physical and cyber systems and assets that are so vital to the United States that their incapacity or destruction would have a debilitating impact on our physical or economic security or public health or safety.
- Federal Bureau of Investigation (FBI), National Consortium for the Study of Terrorism and Responses to Terrorism: Global Terrorism Database, the University of Maryland, retrieved from https://www.start.umd.edu/gtd/
- Federal Bureau of Investigation (FBI), Internet Crime Report, 2021, retrieved from PDF
- The National Infrastructure Protection Plan (NIPP)—NIPP 2013: Partnering for Critical Infrastructure Security and Resilience, 2013, retrieved from National Infrastructure Protection Plan (NIPP) 2013: Partnering for Critical Infrastructure Security and Resilience (cisa.gov)
The latest in Cybersecurity
Enter your email to get the latest news, updates,
and content on cybersecurity.
"*" indicates required fields


