
Preparing for Cybersecurity Maturity Model Certification
As we continue to consult with Organizations Seeking Certification (OSC) that are preparing for the CMMC Level 2 assessment for certification, we find that the non-technical CMMC practices (a.k.a., NIST SP 800-171 security controls) tend to be glossed over. It’s easier to focus on technical controls with tangible solutions (mechanisms, as NIST and CMMC call them) than to evaluate processes’ maturity.
Organizations can easily fall into the trap of treating NIST or CMMC self-assessments as a TVA (an aged acronym), believing that if all technical controls are implemented, it will pass a CMMC Level 2 third-party assessment. However, CMMC certification is more than a technical vulnerability assessment or implementation of all tangible technical controls, the fun, touchy-feely, geeky stuff like firewalls, anti-virus, VPNs, MFA, etc.
Process-based Controls for CMMC Compliance
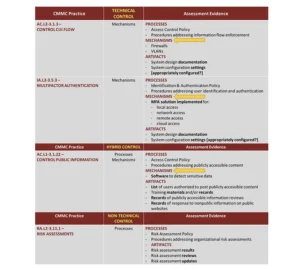
We’ve seen a trend where an OSC has conducted a self-assessment based on NIST SP 800-171 that was heavy on evaluating technical controls. In effect, it was an incomplete evaluation of controls. Although non-technical controls were evaluated, they were documented as implemented based on improper assumptions. Additionally, the assessment results were used to upload a perfect or nearly perfect SPRS score, although the self-assessment did not correctly address all “process-based” controls. See the table for samples.
It can be easy to brush off those non-technical (process-based) controls, such as many of those in the Risk Assessment (RA), Security Assessment (CA), and Personnel Security (PS) CMMC domains. These controls (a.k.a., CMMC practices) tell a story. For example, RA and CA are intrinsically tied, as they tell the story from a life cycle approach from security control assessments (CA) to vulnerability identification (CA) to risk assessment (RA) to risk treatment (RA), etc. Assessors will expect OSCs to be able to showcase (“show and tell”) their processes through policies, processes, procedures, and artifacts.
NIST SP 800-171A and CMMC Assessment Guide
Don’t get caught in the trap that NIST SP 800-171 or CMMC assessments are an exercise in implementing mechanisms to comply with technical control requirements. The non-technical controls, which require the attention of both technical and non-technical subject matter experts, must also be appropriately addressed based on NIST SP 800-171A and CMMC Assessment Guide for Level 2 requirements. This requires non-technical staff, including human resources, facilities manager, marketing, etc.
Happy assessing!
The latest in Cybersecurity
Enter your email to get the latest news, updates,
and content on cybersecurity.
"*" indicates required fields




