The Dichotomy of Strengthening Security and Maintaining an Open Environment of Information
Institutions of Higher Education (IHE) face unique cybersecurity challenges as much as those of commercial and government sectors. The main challenge lies in the dichotomy between strengthening cybersecurity practices while maintaining an open academic environment that encourages the free sharing of information. Additionally, IHE networks are designed to accommodate diverse missions and circumstances, including classrooms, research facilities, administrative functions, faculty needs, student dorms, and athletic facilities. Moreover, IHE must navigate multiple compliance demands, which are increasing at both state and federal levels.
Universities and colleges require a top-down strategy to address today’s cybersecurity challenges.
Top Cybersecurity Challenges

1. Culture of open sharing of information
IHE’s foundation is to share knowledge, which is increasingly running counter to cybersecurity efforts to protect data. More pointedly, information technology (IT) and cybersecurity stewards are responsible for securing the learning environment, which is diametrically opposed to those responsible for ensuring a conducive learning environment for students and researchers. As a result, this culture keeps the IT and cybersecurity professions in an uncomfortable position among faculty, researchers, and university administration.
2. Diverse environment with contrasting objectives
The IHE environment has many players with varying objectives. In most cases, they all share the same common IT network. Administrators, support staff, faculty, researchers, third-party vendors, students, and other stakeholders share the same network exposing their unique risks to the entire campus.
Example threats include, but are not limited to:
- Students access university resources via personal devices—the same devices that use risky applications from the public Internet. Dorm rooms, in particular, are a risky entry point to the campus network.
- Faculty install unvetted or unapproved applications onto university assets, potentially exposing malware to the campus network.
3. Open network, open risk
Numerous stakeholders access the campus network, which processes a broad range of traffic and carries data with varying protection requirements. Data segmentation ensures that only authorized stakeholders can access their data. As with the examples above, dorm rooms, payment systems, administrative systems, and research systems must be set up in separate zones to reduce the risk of compromise. An open network would make it impossible to meet federal and state security, privacy, and IT financial compliance requirements.
4. Multi-compliance demands
The demands on IHE to meet compliance requirements seem to be never-ending. At a minimum, the demand to meet multiple compliance requirements is increasing along with deeper scrutiny into maintaining compliance. IHE has many partnerships and contracts, all of which may come with their own compliance requirements. Universities are struggling to balance multiple mandatory cybersecurity frameworks to measure compliance. Plus, it is resource intensive.
5. Lack of resources
Achieving IT and cybersecurity objectives proves challenging in light of resource constraints, particularly due to the understaffed, under-resourced, and overworked nature of IT and cybersecurity personnel. IHE continuously seeks avenues to enhance staff effectiveness and efficiency to address security, privacy, and compliance requirements. In other words, they strive to accomplish more with limited resources.
Addressing the Challenges
SecureStrux has a proven methodology to help IHE address recurrent challenges through a lifecycle approach that assesses, secures, and defends the environment. This strategy partners with the higher education community to develop an end-to-end solution by creating a roadmap to address weaknesses across the entire campus’s cybersecurity requirements and infrastructure. SecureStrux works with all stakeholders to ensure that cybersecurity is threaded throughout the fabric of the university.
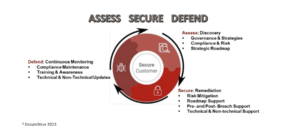
Savvy Experts Who Tackle the Challenge
With a team of cybersecurity experts possessing extensive knowledge, business acumen, and relevant skill sets, SecureStrux offers valuable assistance to universities in effectively managing cybersecurity challenges at every stage. SecureStrux works within the resource constraints to develop and implement a comprehensive strategic roadmap that improves the university’s cybersecurity posture. More importantly, through partnership, the university will realize quantifiable gains in tackling the challenges.
SecureStrux works under a one-team attitude with a sharp focus on achieving results.
Through a diverse leadership and technical team of cybersecurity professionals, colleges and universities receive a singular balance of deep and broad expertise.
Cost-Effective and Rewarding Partnership
Partnering with SecureStrux realizes the benefits of outsourcing the necessary activities to work through cybersecurity and compliance challenges. Seasoned cybersecurity experts and thought leaders work together to understand, prioritize, and manage cybersecurity needs in the context of the university’s business, academic, and research goals, addressing the issues of today and preparing for the challenges of tomorrow.
SecureStrux™ recognizes the vital work conducted by universities nationwide and is proud to support institutes of higher learning to meet their requirements.
Sources
- Wangen, Gaute Bjørklund, February 2, 2021, A Systematic Review of Cybersecurity Risks in Higher
Education - Steve Scholz, William Hagen and Corey Lee, June 22, 2021, The Increasing Threat of Ransomware in
Higher Education - SecureStrux, 2023


