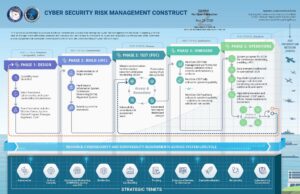
Breaking Down the Department of War’s New Cybersecurity Risk Management Construct (CSRMC): 5 Phases and 10 Tenets
As outlined within the DoW announcement dated September 24th, 2025, DoW is looking to replace the Risk Management Framework with a “modernized” framework or “construct” that focuses more on current battlefields in both physical and cyber space. The CSRMC has 5 Phases and 10 guiding principles/tenets. Below is a breakdown and interpretation of the 5 Phases and the 10 strategic tenets as outlined within the DoW announcement and additional DoD CIO CSRMC supplemental document.
CSRMC Phases
Phase 1: Design Phase
Security is embedded at the outset, ensuring resilience is built into system architecture. (RMF Step(s): Prepare, Categorize, Select)
- Capability need identified: (Put another way, Identify the needs/capabilities for operations in dynamic battlefield.)
- What this means: This will most likely tie directly to an operational or technological need from the warfighter or a gap that needs to be filled in warfighter capabilities, technologies, or operations. This will apply to “critical warfighter technology and operations.”
- Select functional cybersecurity, and cyber survivability requirements: (Put another way, Select security controls/requirements that are critical to cyber resilience in a dynamic battlefield.)
- What this means: Think minimum viable products (MVPs) that gets the job done and can still operate while under cyber attack (requires forethought into cyber resiliency for wartime operations). What are the most critical points of failure in a technology or operation and how can those be made resilient to cyber attacks?
- Team formation includes Mission Owner, System Owner/Program Manager, Engineers, CSSP: (Put another way, Ensure that top to bottom communication of product operations and critical technologies have the necessary stakeholder buy-in throughout the Development, Test, and Production of critical technologies and operational systems.)
- What this means: This means DoW will expect a greater level of communication between the Engineers and Design Teams creating the products and the Management Teams (Program Managers, Key Stakeholders, etc.) and the Security/Cybersecurity Teams to ensure that messaging, funding, and operations are moving forward to support the warfighter capabilities in a more focused and direct way.
Phase 2: Build Phase
Secure designs are implemented as systems achieve Initial Operating Capability (IOC). (RMF Step(s): Implement)
- Implementation of Requirements
- What this means: Currently this is a bit ambiguous and could mean implementing the contractual and/or mission requirements for the warfighter product or this could mean implementing the requirements of the necessary security controls that apply to the specific technology, application, software, or operational systems.
- Feed data to Information System Continuous Monitoring (ISCM) Alignment System:
- What is means: Based on research, this ISCM system may be aligned with NIST SP 800-137 Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations (dated September 2011). As outlined within 800-137, ISCM necessitates the following:
- Maintaining situational awareness of all systems across the organization;
- Maintaining an understanding of threats and threat activities;
- Assessing all security controls;
- Collecting, correlating, and analyzing security-related information;
- Providing actionable communication of security status across all tiers of the organization; and
- Active management of risk by organizational officials.
- This could be a new compliance system similar to eMASS that is being fed real-time or near-real-time data from the DoDIN and DIB contractors to determine the active risks to networks, systems, and operations across the DoW. Much is still unknown.
- What is means: Based on research, this ISCM system may be aligned with NIST SP 800-137 Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations (dated September 2011). As outlined within 800-137, ISCM necessitates the following:
- Submit system for evaluation
- What this means: Assuming the Information System Continuous Monitoring Alignment System (ISCMAS) is supposed to be like eMASS, submitting an organization’s current System Security Plan (SSP) may include similar data such as network designs, ACLs, vulnerability scans, identified risks and mitigation strategies, etc. It is currently unknown as to who would be responsible for submitting, who would be responsible for assessing, and who would be responsible for authorizing.
Phase 3: Test Phase
Comprehensive validation and stress testing are performed prior to Full Operating Capability (FOC). (RMF Step(s): Assess)
- Mission customization for ISCM
- What this means: This will most likely be similar to RMF Categorization for Confidentiality, Integrity, and Availability (C.I.A) but be based on certain DoW defined mission criticalities based on technologies, operations, or system requirements.
- Penetration testing (high risk systems)
- What this means: This will most likely apply to high risk DoDIN systems and DIB system connecting to the DoDIN (i.e., NIPR, SIPR). This will most likely NOT apply to standalone and/or classified DIB system that do not connect to the DoDIN.
- Automated test report dashboard analyst
- What this means: As stated above, the likely outcome of an ISCM system will be a real-time or near-real-time reporting system for each authorized connection that delivers a dashboard of current risks, vulnerabilities, and remediations (POA&Ms) that can be viewed by SCAs and organizations alike.
- Vulnerability remediation & assessment team
- What this means: This will probably mean a much larger emphasis on purple team integrations (Blue team defender and Red team aggressor) across the DoD/W, DoDIN, and DIB. Security Control Assessors (SCAs) or the new equivalent will be focused on vulnerability and risk remediation rather than specific control compliance.
Phase 4: Onboard Phase
Automated continuous monitoring is activated at deployment to sustain system visibility. (RMF Step(s): Authorize)
- NextGen CSSP risk management performs risk review, validates critical controls and mandatory artifacts: (Put another way, Use AI tools to perform validation of control implementation and highlight critical controls, flaws, or remediation actions.)
- What this means: The DoD/W will look to implement AI driven compliance tools that provide speed and accuracy across an assessment and point out critical flaws in a system documentation, control implementation, or vulnerability remediation.
- NextGen CSSP fully onboards system/capability OR NextGen CSSP partially onboards system/capability – isolation, re-sensoring, additional risk review: (Put another way: AI compliance tool will evaluate and authorize a system or give partial/conditional authorization to some or all of a system based on risk evaluation and vulnerability management.)
- What this means: Again, heavy reliance on AI tools to parse through controls, documentation, vulnerability scans, remediation strategies, to identify flaws, errors, or critical deficiencies during an assessment/evaluation prior to system authorization.
Phase 5: Operations Phase
Real-time dashboards and alerting mechanisms provide immediate threat detection and rapid response. (RMF Step(s): Monitor)
- System accepted for ISCM for continuous monitoring enabling cATO.
- What this means: Once a system has made it through the assessment process it is approved and authorized for a Continuous Monitoring ATO.
- Data elements redirected to operational ISCM.
- What this means: As stated above, this will most likely be real-time or near-real-time data from each system regarding vulnerabilities and risks.
- Repeatable playbook to manage real-time risk monitoring via automated dashboards and alerts.
- What this means: As stated above, the driving factor will be real-time vulnerability and risk remediation data that can be viewed in real-time to any systems on or connected to the DoDIN.
- High risk is elevated and addressed – CSSP watch officer makes decision to disconnect.
- What this means: This means that at a high enough level/authority, if a system poses too high a risk, it can and/or will be disconnected (in real-time) from the DoDIN. This means if an entire agencies fails to maintain appropriate cybersecurity posture, it can be disconnected from the DoDIN.
CSRMC Strategic Tenets
DoW/DoD CSRMC Tenets. In no particular order:
-
Automation: Automate to enhance risk management by streamlining processes, reducing human error, and improving efficiency.
- Critical Controls: Adhere to identified critical controls, and adaptive recovery strategies strengthen defenses to ensure operational continuity and protect sensitive assets.
- Continuous Monitoring (CONMON), Control, and ATO: Provide real-time visibility into threats, vulnerabilities, and compliance gaps through continuous monitoring.
- DevSecOps: Integrate security and automation through continuous development, testing, and deployment to accelerate delivery safely.
- Cyber Survivability: Safeguard against cyber threats, disruptions, and data breaches through strong encryption, multi-factor authentication, continuous monitoring, and incident response planning.
- Training: Enhancer ole-based training program for RMF practitioners to ensure consistent performance, cybersecurity knowledge, and standards.
- Enterprise & Inheritance: Share security controls, policies, or risks to increase adoption proven frameworks, reduce compliance burdens, and maintain operational consistency.
- Operationalization: Strengthen our defense against evolving threats through threat detection, incident response, compliance management, and proactive monitoring.
- Reciprocity: Accept each other’s security assessments to reuse system resources and/or to accept each other’s assessed security posture to share information.
- Cybersecurity Assessments: Establish comprehensive cybersecurity assessment programs that integrate threat-informed testing methodologies with mission-aligned risk management processes.
How does this new CSRMC match with current DoD/W RMF implementation and interpretation? What are the differences and where will DIB fall in meeting the requirements? Below is a breakdown of the differences between current RMF requirements (NIST SP 800-37 and 800-53) and CSRMC requirements.
| CSRMC Tenet | Current RMF and DCSA DAAPM | Implications Under CSRMC | Considerations for DCSA and DAAG |
|---|---|---|---|
| 1. Automation | eMASS is still heavily dependent on manual data entry and document uploads, although import and export features exist. | CSRMC expects automation to drive the process. Security evidence, scanning results, and POA&M status are intended to feed directly into dashboards with minimal manual handling. | Automation Expectations eMASS: Manual-heavy. CSRMC: Automation-driven.DCSA will need to:1. Support automated data feeds 2. Reduce reliance on manual artifact uploads 3. Possibly overhaul eMASS architecture |
| 2. Critical Controls | RMF requires implementation of the entire NIST SP 800-53 baseline with overlays. | CSRMC concentrates on a smaller number of high-value controls. These include multi-factor authentication, encryption, logging, and timely patching. Contractors will be held to stricter performance standards for this reduced set. | Control Selection eMASS: Categorizes and selects controls based on overlays or C.I.A. risks.CSRMC: May implement controls based on ISCM system.DCSA will need to:1. Replace security control selection process 2. Replace eMASS 3. Implement security control approval process |
| 3. Continuous Monitoring (CONMON), Control, and ATO | Monitoring under DAAPM is largely periodic. ISSMs update eMASS annually and DCSA conducts periodic reviews. | CSRMC treats monitoring as a continuous process. Systems remain authorized only as long as continuous data feeds into CSSP dashboards show acceptable risk. Elevated risk or missing data can lead to immediate operational action, including disconnection. | Continuous Monitoring and Conditional ATO (cATO).
DAAPM: Monitoring is periodic; eMASS updates are annual. CSRMC: Monitoring is continuous. DCSA must: 1. Integrate with CSSP dashboards |
| 4. DevSecOps | DAAPM does not explicitly address DevSecOps. Implementation and assessment are viewed as discrete activities before authorization. | CSRMC requires security to be integrated into development pipelines. Automated configuration scanning and security validation within CI/CD workflows are considered essential. | DevSecOps Integration RMF: Security is a pre-authorization activity. CSRMC: Security must be embedded in CI/CD pipelines. DCSA will need to: 1. Understand and assess automated security validation 2. Possibly revise assessment criteria to include DevSecOps practices |
| 5. Cyber Survivability | DAAPM requires contingency and incident response plans that emphasize recovery. | CSRMC emphasizes the ability to operate while under attack. Systems are expected to demonstrate resilience and continuity of mission functions during active cyber events. | Cyber Survivability Focus DAAPM: Focuses on recovery after incidents.CSRMC: Emphasizes resilience during attack.DCSA will need to:1. Evaluate systems for mission continuity under duress 2. Possibly require live demonstrations or simulations |
| 6. Training | DAAPM requires role-based training for ISSMs, ISSOs, and related staff. | CSRMC extends training expectations across the full lifecycle. Developers, operators, and CSSP analysts are all expected to meet consistent role-based training standards. | Expanded Training Requirements
RMF: Role-based training for ISSMs/ISSOs. CSRMC: Training extends to developers, operators, CSSP analysts. DCSA may need to: 1. Update training guidance |
| 7. Enterprise & Inheritance | eMASS supports inheritance and use of common control providers, but use is inconsistent and often optional. | CSRMC makes inheritance the expectation. Enterprise services such as CSSP monitoring and DISA enterprise solutions are intended to be consumed by default rather than recreated locally. | Enterprise Services and Inheritance
Today: Inheritance is optional and inconsistently applied in eMASS. CSRMC: Inheritance becomes mandatory. DCSA will need to: 1. Promote use of DISA-provided services (e.g., CSSP, HBSS, ACAS) |
| 8. Operationalization | RMF activities are treated as a compliance process separate from daily operations. | CSRMC embeds cybersecurity into operations. Cyber risk management is performed continuously by CSSPs and commanders, and operational decisions can be based on current cyber risk. | |
| 9. Reciprocity | DAAPM allows reciprocity but in practice each Authorizing Official often repeats or supplements the review. | CSRMC intends reciprocity to be routine. Acceptance of one component’s authorization by others will be expected, which places more weight on the quality of the original package and the accuracy of monitoring data. | Reciprocity Becomes the Norm
RMF: Reciprocity is allowed but rarely practiced. CSRMC: Reciprocity is expected. DCSA will need to: 1. Accept authorizations from other components |
| 10. Cybersecurity Assessments | DAAPM requires control validation, submission of artifacts, POA&Ms, and DCSA on-site validation. | CSRMC reframes assessments to be threat-informed and mission-focused. The emphasis is on red team activities, continuous vulnerability scanning, and assessment of mission impact rather than checklist compliance. | DCSA’s Role in Assessments Will Shift:
Current DAAPM/RMF: DCSA performs on-site validations, reviews artifacts, and checks compliance. Under CSRMC: DCSA will need to pivot to threat-informed assessments, including: 1. Red team exercises |
Some additional considerations for DIB and the DCSA classified space:
Timing Conflict with DAAG Release
DAAG (DCSA Assessment and Authorization Guide) is reportedly set to be released around October 1st, but CSRMC was just announced.
This creates a potential obsolescence issue: DAAG may be outdated before it’s even published, as it’s based on RMF principles that CSRMC is now replacing.
If DAAG is released as planned, it may serve as a transitional document, but will likely need:
-
- Rapid updates
- Supplemental guidance
- Alignment with CSRMC principles
In summary, the integration and implementation of the new CSRMC will likely be slow as this is moving at the speed of government.
Some key takeaways for the DIB are that this will most likely apply to enterprise systems and critical infrastructure connected to the DoDIN, or those providing critical technologies directly tied to warfighter capabilities. This will most likely not impact standalone classified systems that have no connection to the DoDIN or to the internet.
A classified MUSA laptop will probably not be required to implement DevSecOps or Reciprocity as these aren’t feasible for such small systems with no external connections. DCSA is in the midst of releasing the DAAG, which is their interpretation of NIST SP 800-53 Rev 5 and has been in the works for more than 3 years.
From an undisclosed DCSA source, CSRMC will not likely be implemented for a very long time given the amount of time it took to implement DAAPM V2 to DAAG.
While the rollout of CSRMC may take years, it’s important for defense contractors and organizations within the DIB to start preparing now. Understanding how these frameworks align with current compliance requirements and anticipating their eventual impact can help you stay ahead of the curve rather than scrambling once enforcement begins.
At SecureStrux, we specialize in helping organizations navigate evolving defense cybersecurity requirements—from NIST 800-53 and DAAPM to emerging constructs like CSRMC. Our experts can help you assess your current posture, close compliance gaps, and build a resilient, future-ready security program. Contact us today to set up a meeting.
The latest in Cybersecurity
Enter your email to get the latest news, updates,
and content on cybersecurity.
"*" indicates required fields