NIST Releases Concept Paper to Guide Development of CSF 2.0
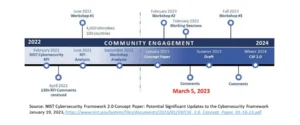
The National Institute of Standards and Technology (NIST) has posted a concept paper titled, “Potential Significant Updates to the Cybersecurity Framework,” providing an update on the cybersecurity framework (CSF). NIST has also announced its plan for scheduling virtual and in-resident workshops starting in February. The first draft of CSF 2.0 will be released this summer. In the meantime, the concept paper is open for comment until March 3, 2023.
The concept paper can be found here: NIST CSF 2.0 Concept Paper
What is the NIST Cybersecurity Framework (CSF)?
NIST CSF was developed with a focus on industries vital to national and economic security, including the sixteen critical infrastructure (CI) sectors (e.g., health, energy, defense industrial base (DIB), chemical, emergency services, financial, etc., to name a few). NIST CSF, more affectionately known as “Framework,” was developed in response to Executive Order 13636 (“Improving Critical Infrastructure Cybersecurity,” February 2013) to improve the protection of the nation’s CI from cyber-attacks. However, while the Framework is focused on CI organizations, non-CI organizations, both public and private, have voluntarily adopted the framework based on its flexibility and scalability.
NIST CSF typically aids in the measurement of an organization’s cybersecurity program. Since its original publishing almost a decade ago (2014), the adoption of NIST CSF has grown rapidly due to many organizations viewing the framework as an industry best practice. Some of the top benefits of NIST CSF include (not all-inclusive):
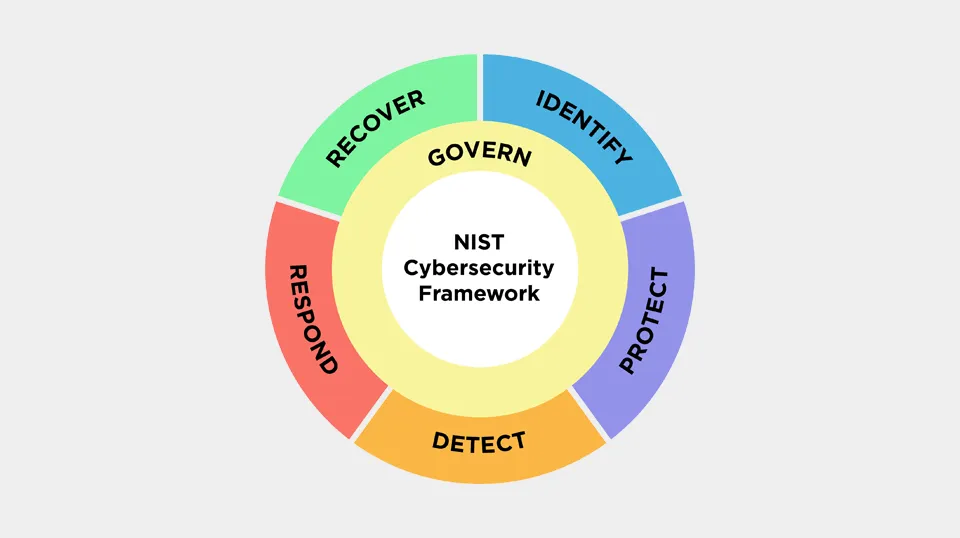
- GOVERNANCE: Provides a foundation for developing and maintaining organizational cybersecurity strategies.
- COMPLIANCE: Measures compliance requirements across multiple frameworks, laws, and regulatory mandates.
- RISK: Provides an adaptive model for managing cybersecurity risk.
- BUSINESS & TECHNICAL SYNERGY: Aids in bridging the gap between techno-jargon and business speak.
While NIST CSF is not perfect (that’s for another article), it provides a solid foundation with a common language for strengthening and measuring an organization’s cybersecurity program. NIST CSF provides a conceptual front end to NIST SP 800-53a.
What are these significant changes about?
The current version of NIST CSF is version 1.1, titled “Framework for Improving Critical Infrastructure Cybersecurity,” which focuses on critical infrastructure. The intent of NIST CSF 2.0 is to expand its appeal and capabilities beyond the critical infrastructure to cover organizations across public and private sectors between industry, higher education, and local, state, and federal governments. NIST CSF’s main objective is to ensure that NIST CSF 2.0 is beneficial for all organizations, regardless of industry sector, complexity, type, or size to address today’s cybersecurity challenges. Based on the concept paper, the path to NIST CSF 2.0 hinges on the following proposed changes:
- Explicitly recognize the CSF’s broad use to clarify its potential applications.
- Scope the CSF to ensure it benefits organizations regardless of sector, type, or size.
- Increase international collaboration and engagement.
- Retain CSF’s current level of detail.
- Relate the CSF clearly to other NIST frameworks.
- Improve the understanding of the relationship to risk management.
- Add a new “Govern” Function to emphasize cybersecurity risk management governance outcomes.
- Emphasize the importance of cybersecurity supply chain risk management (C-SCRM).
- Leverage Cybersecurity and Privacy Reference Tool for online CSF 2.0 Core.
- Use Informative References to provide more guidance to implement the CSF, including securing controlled unclassified information (CUI), cloud computing, Internet of Things (IoT), Operational Technology (OT), and zero trust architecture (ZTA), to name a few.
- Expand guidance on framework implementation.
- Add implementation examples of concise, action-oriented processes and activities to help achieve outcomes.
- Develop a CSF Profile Template for organizations to develop CSF Profiles.
How can you get involved?
If you would like to help formulate NIST 2.0, NIST has a feedback period until March 3, 2023. Feedback and comments should be directed to cyberframework@nist.gov.
Some questions that NIST would like stakeholders to consider when providing feedback include the following:
- Do the proposed changes reflect the current cybersecurity landscape (standards, risks, and technologies)?
- Are the proposed changes sufficient and appropriate? Are there other elements that should be considered under each area?
- Do the proposed changes support different use cases in various sectors, types, and sizes of organizations (and with varied capabilities, resources, and technologies)?
- Are there additional changes not covered here that should be considered?
- For those using CSF 1.1, would the proposed changes affect the Framework’s continued adoption, and how?
- For those not using the Framework, would the proposed changes affect the potential use of the Framework?
If you would like to learn more about how to use the “Framework” or avoid potential pitfalls, please contact SecureStrux.
The latest in Cybersecurity
Enter your email to get the latest news, updates,
and content on cybersecurity.
"*" indicates required fields





