Introduction
In today’s digital landscape, cybersecurity is paramount, especially for organizations within the Defense Industrial Base (DIB). The Cybersecurity Maturity Model Certification (CMMC) is a critical framework designed to enhance the protection of sensitive information. SecureStrux, a leading cybersecurity firm, offers comprehensive CMMC services to help organizations achieve and maintain compliance.
Authorized C3PAO Services
 As an authorized C3PAO (Certified Third-Party Assessor Organization), SecureStrux is equipped to conduct official CMMC assessments. Our team of certified CMMC assessors (CCA) and certified CMMC professionals (CCP) provides objective and tailored evaluations to ensure organizations meet the stringent requirements of CMMC.
As an authorized C3PAO (Certified Third-Party Assessor Organization), SecureStrux is equipped to conduct official CMMC assessments. Our team of certified CMMC assessors (CCA) and certified CMMC professionals (CCP) provides objective and tailored evaluations to ensure organizations meet the stringent requirements of CMMC.
SecureStrux also provides comprehensive CMMC consultancy services, and a range of services tailored to meet the specific needs of organizations seeking CMMC certification. Our services are based on an Assess–Secure–Defend methodology, ensuring a thorough and effective compliance journey.
Assess
- Gap Analysis: SecureStrux conducts detailed assessments to identify gaps in your current cybersecurity posture. This includes evaluating Controlled Unclassified Information (CUI) boundaries and existing security measures.
- Readiness Reviews: Before formal assessments, SecureStrux offers readiness reviews (mock assessments) to prepare organizations for the certification process.
Secure
- Technical and Non-Technical Remediation: SecureStrux assists with implementing necessary changes to address identified gaps. This includes consultation efforts on both technical solutions and administrative controls.
- Documentation Development: SecureStrux will help develop and refine cybersecurity documentation to align with CMMC requirements.
Defend
- Continuous Monitoring: SecureStrux provides tailored ongoing monitoring services to ensure continued compliance with CMMC standards. This proactive approach helps maintain a robust security posture.
Safeguard Controlled Unclassified Information using Microsoft Cloud
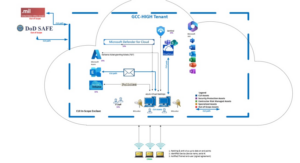
*EXAMPLE*
SecureStrux utilizes Microsoft’s GCC High secured cloud solution for our cybersecurity compliance services. GCC High is a version of Microsoft 365 designed to meet the stringent security and compliance requirements of the U.S. government and defense contractors. It provides enhanced CUI data protection and compliance features, making it suitable for organizations handling sensitive information.
Additionally, SecureStrux uses and recommends Microsoft Azure Virtual Desktop (AVD) deployments. Why? AVD is a robust solution for delivering virtual desktops and applications to DOD contractors. AVD enables the Defense Industrial Base to provide secure, scalable, and cost-effective virtual desktop infrastructure (VDI) from Microsoft’s secured cloud. Learn all about Microsoft’s AVD.
Key Features of Azure Virtual Desktop
- Multi-Session Windows 10 and 11: AVD is the only service that offers multi-session Windows 10 and 11, allowing multiple users to share the same virtual machine while maintaining a familiar Windows experience.
- Scalability and Flexibility: Organizations can scale their virtual desktop environments up or down based on demand, optimizing costs and ensuring efficient resource usage.
- Enhanced Security: AVD integrates with Microsoft Entra ID (formerly Azure Active Directory) and supports multi-factor authentication (MFA) to enhance security. It also includes conditional access and role-based access control (RBAC).
- Seamless Integration with Microsoft 365: Users can access Microsoft 365 apps and services seamlessly, enhancing productivity and collaboration.
- Simplified Management: AVD provides centralized management through the Azure portal, allowing IT administrators to easily deploy, manage, and monitor virtual desktops and applications.
Architecture and Components of AVD
- Control Plane: Managed by Microsoft, the control plane includes web access, gateway, connection broker, diagnostics, and extensibility components.
- Host Pools: Organizations can create host pools, which are collections of Azure virtual machines registering to AVD as session hosts. These pools can be configured for personal or pooled desktops.
- FSLogix Profile Containers: FSLogix technology ensures a consistent experience across sessions, reducing login times and simplifying user profile management.
- Networking: AVD supports integration with on-premises networks via Azure ExpressRoute or VPN, providing secure and reliable connectivity.
Use Cases
- Remote Work: AVD enables employees to access their desktops and applications from anywhere, ensuring business continuity and flexibility.
- Seasonal Workforce: Organizations can quickly scale up virtual desktops for temporary or seasonal workers, then scale down when demand decreases.
- BYOD (Bring Your Own Device): Employees can use their personal devices to access corporate resources securely, reducing hardware costs for your organization.
- Application Compatibility: AVD supports legacy applications that may not be compatible with newer operating systems, extending the life of critical business applications.
Benefits of AVD
- Cost Efficiency: Pay-as-you-go pricing and scalability ensure optimized costs.
- Improved Productivity: Users can access desktops and applications from any device, enhancing flexibility and productivity.
- Enhanced Security: Built-in security features and integration with Microsoft security solutions help protect sensitive data and ensure compliance.
- Simplified IT Management: Centralized management and automation reduce the administrative burden on IT teams.
Conclusion
SecureStrux believes that Microsoft’s Azure Virtual Desktop (AVD) is a powerful solution for DIB companies looking to modernize their IT infrastructure, support remote work, and enhance security. By leveraging AVD, businesses can provide a flexible, scalable, and secure virtual desktop environment that meets the needs of today’s dynamic workforce.


